The four women who were promoted--Amy Hood, Julie Larson-Green, Lisa Brummel, and Tami Reller--are now in four of Microsoft's 13 Executive Vice President positions. The move has already garnered some positive press for the tech giant, which is not altogether undeserved.
But if you cast an ever-so-slightly critical eye at the facts, there's still plenty of room for improvement. First of all, three of these new executives are in positions that don't directly touch on any Microsoft development teams: Brummel is EVP, Human Resources; Hood is EVP and Chief Financial Officer; Reller is EVP, Marketing. Only Larson-Green, in her position as EVP of Devices and Studios, which oversees the Xbox and Surface, is directly responsible for development teams and has a software development background.
While we certainly applaud any lifting of the glass ceiling for women within Microsoft, it’s also fairly self-evident that to get more women programmers, big-cap companies may need more women managing programmers. In fairness, only four of Microsoft's 14 executive positions (counting CEO Steve Ballmer) are explicitly development-related. The 1:3 women to men ratio fits company-wide and even industry-wide trends, which I've previously covered in this tracking story. (To see stats, scroll down to the entry below entitled “Hard Numbers.”)
Still, it's not all fun and games for Larson-Green. In fact, it's games that have already presented one major headache. After it was revealed that she would be stepping in for Don Mattrick in charge of Xbox, online news comment threads were filled with all manner of vitriol aimed at Larson-Green for nothing more than her gender. It’s well-documented that gaming is a particularly male-dominated subset of the technology world, with plenty of room for improvement, but frankly we didn’t expect this severe a reaction.
Company-wide, Microsoft’s employee gender breakdown is under 25% female, and while the company doesn’t offer gender breakdowns by job title, I’d wager that the ratio of females in programmer roles to non-programmer roles is much lower than the same ratio for male Microsoft employees. (The disparity is likely offset in the overall numbers by Microsoft’s enormous publishing, marketing, and publicity arms, which in most large companies are traditionally more populated by women.) Microsoft isn’t a lone pariah of gender inequality in the tech world--it’s just archetypal of the sort of frat-like companies we hope will change.
Previous Updates
Why Can’t Female Tech Founders Get Funding?
July 16, 2013
Ross Baird founded the Village Capital startup accelerator program four years ago to assist mission-driven companies tackling major social problems, who might not otherwise get access to capital. At the end of each program, the 15 or so companies in a cohort select two of their peers to receive a $50,000 investment.
Now he has a problem. Roughly half of the 250 Village Capital alumni companies have a female cofounder, but those companies are 50% less likely to get follow-on funding than those with all-male founding teams. This is in spite of the fact that female-led Village Capital companies are 15% more likely to be profitable and 78% more likely to be selected by their peers for investment.
“The process favors entrepreneurs who are more substantive and less flashy,” says Baird. “We find that women tend to under-promise, over-deliver, hit milestones but are maybe not as free to brag about themselves up on stage. Men, and I say this fully aware of being one, will oversell anything. Women undersell and this is a problem particularly in fundraising across our alumni. The shift in power dynamic in peer selection corrects for some of that. One of our female entrepreneurs has said that she often felt like she didn't get a fair shake in the traditional investment process in that she wasn’t really given the time to demonstrate her value, to demonstrate what she was creating.”
Baird thinks that the power imbalance between investors and founders is a bad thing for everyone. “Many startups are trying to figure out what investors will invest in. There is an overemphasis on 'What do investors like?' and less emphasis on 'What value can we provide to the world?' Raising money should not be your primary goal as a startup. We say that if you build a company which solves a major problem and people are willing to pay you to get the problem solved then investment will come. Investment is the result of achieving your goals. It shouldn't be the goal itself.”
As a result, Village Capital’s program concentrates on customer validation, acquisition, and revenue rather than pitching to investors. On top of the peer-to-peer review process, this emphasis on customers may favor women. “'We will get as many users as possible and we will figure out how to monetize them later' is not in the long term a successful business strategy. A lot of what we do in the program is distinguishing between customers and users. In the peer-to-peer process, customer acquisition rather than user acquisition is rewarded,” says Baird.
That peer-to-peer review process involves three open peer ranking sessions where each company ranks the others based on team, product, customer, financials, scale, and return of capital. The final session results in the selection of the teams which get an investment. Baird insists that that process is more productive for everyone than the traditional investment model.
“In the prize mentality or the ‘get the investment’ mentality in a startup competition, two people get funding, 15 people get skewered and ripped apart by people trying to make themselves look good, and the non-winners just don't get anything,” explains Baird. “In the peer-reviewed process everyone gets something out of it. Entrepreneurs when they give feedback to each other are very thoughtful because they care a lot about each other and if they are unfair to each other it comes back to them. The process is productive even for the non-winners.” Could this emphasis on collaboration, rather than competitive pitching, be the key to the success of female entrepreneurs in the Village Capital program?
When I ask Baird to choose his favorite Village Capital graduate he doesn’t hesitate. “Kickboard. Peer selected from the first program. The founder is a woman who is a teacher and coder and she has a data management process which allows teachers to manage student performance data so they can improve teaching. She didn't set out to be an entrepreneur. She built this as a teacher to solve problems for other teachers.”
Kickboard founder Jen Medbery tried to get the company off the ground for a year before finding Village Capital. Four years later Kickboard has raised $2 million in mainstream capital. “To see her not raising funds in the traditional angel investment world but being the overwhelming favorite of her peers, getting her first investment peer selected and becoming incredibly successful in solving major problems in U.S. education is a story I am really excited about,” says Baird.
This Simple Toy Shows Why Girls Hate Engineering
July 10, 2013
Growing up in Ireland my three siblings and I had a favorite game; We called it James Bond. One of us would play the coveted role of secret agent, and the remaining siblings tried to stop them from snatching some top secret papers.
The twist? We’re all sisters--not a James in the bunch.
As children, nobody ever told us that it was strange for four girls to impersonate James Bond plots. Yet we girls do get the message early and often that engineering is not something for us. The CEO of website builder Moonfruit, Wendy Tan White, recently described in the Guardian how she speaks at schools about careers in technology:
"Raise your hand if you want to work in technology," I ask students. Predictably, but sadly, no hands go up. But when I ask girls to raise their hands if they like Facebook, every arm in the room reaches for the sky. The "geeky" label is still attached to technology in schools, so it's little wonder that students can be indifferent to the subject: it's not presented in a way that's appealing.There needs to be a greater focus on showing what technology allows you to do: cross geographical boundaries; make stuff; unleash your creative side; talk to friends; and share your latest musical creation.
That brings us back to Goldie Blox, a construction kit for girls from the age of six up. CEO Debbie Sterling is herself a Stanford engineering graduate, and after talking to young girls about the toys they love most, she came to a realization: Girls love to read because they love stories. My sisters and I were all voracious readers. “Most construction and engineering kits, which are touted as ‘technical and numerical toys,’ don’t include the storytelling that appeals to many girls,” reports Forbes.
So Sterling designed a kit to be used in conjunction with a story book starring a girl inventor called Goldie who builds machines in order to solve problems, in the first book a spinning machine to help her dog chase his tail.
With the Spinning Machine, Sterling introduces girls to the idea of a belt drive and the concept of tension by using a plastic pegboard, spools and ribbon to teach them how to turn one and then multiple wheels as part of a story involving Goldie’s dog Nacho and several other characters.
GoldieBlox reached its $150,000 funding target in the first four days of a Kickstarter campaign last year (It eventually raised $285,811) and Toys ‘R’ Us will stock the $29.99 “GoldieBlox and the Spinning Machine” in more than 600 stores.
This is a generalization of course--but girls are often more interested in machines and technical systems when they are placed in a larger context, where there’s a problem to be solved or an obvious benefit to society. It’s no coincidence that women study medicine in much higher numbers than engineering, even though both tracks are technical; It’s obvious that doctors help people.
Girls don’t just want to have fun--they want to know why.
Why Aren’t All Executives Female?
June 25, 2013
Last month we took a statistical look at how job titles break down by gender. This month we’re looking at why women are not represented at the highest levels of their work sectors. (Read back through our previous updates below if you need to get caught up.)
A study published in the May issue of the Personality and Social Psychology Bulletin may help. It seems to suggest that women don’t take as much credit for their work as their male counterparts, undervaluing their contributions to a project when working with men. From the article’s abstract:
Women gave more credit to their male teammates and took less credit themselves unless their role in bringing about the performance outcome was irrefutably clear (Studies 1 and 2), or they were given explicit information about their likely task competence (Study 4). However, women did not credit themselves less when their teammate was female (Study 3).
The full study is unfortunately behind the ivory tower academic paywall, but Wired U.K. has more details on the study and noted that “teamwork is an essential component to most professional roles, so if women repeatedly undervalue themselves in group situations, in front of coworkers and employers, it could be extremely detrimental to overall job progression.”
This study offers a strong, plausible reason for why women are not as likely to be recognized as leaders in their workplaces: You often have to speak up for your accomplishments in order to advance in your career.
Another bit of research put out last week in the Journal of Evolutionary Biology reveals that female scientists (evolutionary biologists, in the case of this study) don’t present their work at conferences as much as their male colleagues. Apparently, women are underrepresented even in relationship to the gender gap that already exists in science fields. In other words, the percentage of female conference presenters is even lower than the percentage of female scientists.
Apparently, one of the main causes of this underrepresentation was that women turned down conference speaking invitations at nearly twice the rate (50 percent) as men (26 percent). One of the study’s main authors, Dr. Hannah Dugdale, elaborated on the implications of the study's findings:
“It’s important that we understand why this is happening and what we can do to address it--high-quality science by women has low exposure at the international level, and this is constraining evolutionary biology from reaching its full potential. We’re currently investigating the reasons behind this lower acceptance rate--it could relate to child-care requirements, lower perception of scientific ability, being uncomfortable with self-promotion--there are many potential contributing factors.”
It could also be related to the social psychology study above: If women don’t feel as confident in their accomplishments, then they may feel underqualified to speak at international conferences.
Obviously neither of these studies look directly at gender dynamics in the software development space. But looking at both of these studies, it seems like some aspects might apply to software while others might not as much. For instance, it’s definitely true that women coders are underrepresented in conference keynotes. And the observation of Dugdale’s coauthor, Dr. Julia Schroeder, that “[f]ewer women in top positions mean fewer female role models for students who aspire to be scientists” certainly rings true in the software world as well.
On the other hand, depending on what type of developer someone is, they might work on their own a large part of the time, possibly even freelancing from home. In that case, the social psychology of attributing success to male colleagues isn’t as relevant. Of course, many developers work in corporate office jobs where that dynamic could very much still be at play.
In other news, the fact that half of NASA’s eight newest astronaut trainees are women, selected from a pool of over 6,100 candidates, is a good sign. It shows that some progress is being made in STEM fields more generally, especially considering the fact that until now only 10.7% of the people who have been in space are women. With NASA astronauts being the elite of their fields, not to mention role models for every third grader in the country, having more women in space certainly bodes well for the prospect of more role models for women interested in STEM careers.
Minding The Gap: How Your Company Can Woo Female Coders
The software industry has a gender problem. Men far outnumber women, and while most of those men like (dare we say delight in?) having women around the office, the cool-bro rock star nerd culture makes it harder to attract, hire, retain and--most important--listen to women engineers. We'll be tracking successes, conflicts, and visionaries in this vein, and narrate as the status quo changes. We won't stop tracking this story until there are as many women working in software as men.
Why Don't Women In Tech Speak Up?
We’re not the only journalists tracking women’s roles in technology. Laura Sydell, a longtime technology reporter for NPR, covers the intersection of technology and culture, and we caught her story a few weeks ago about the changing lives of female programmers. We asked her to give us the behind-the-scenes scoop on her recent piece profiling prominent developer Sarah Allen, who led the team that created Flash video and now runs a mobile app design firm. Sydell has seen the reality of ingrained sexism and thinks that building momentum is the only way to undo industry habits.
“My take is that it’s about visibility,” Sydell says. “I mean who do you hear about in the news? Who do you see in the news? Twenty percent of programmers are women—that’s a significant number,” Sydell says. But where is the coverage?
One obstacle is that women in tech are sometimes reluctant to talk about sexism (“like it’s a disease they might catch” says Sydell.) She speculates that pointing out a gender disparity at their jobs may not feel like it will ultimately benefit their personal situation. “This doesn’t mean they don’t experience sexism,” Sydell says. “They just want to fit in and they’re working hard to get ahead.”
If her sources are mum about office sexism, Sydell says, they’re even less open about the flaws they see in hiring practices. “I have had some off the record conversations where people are like, ‘well I’m afraid to hire a woman if she’s around childbearing age because we can’t afford for somebody in a startup to take maternity leave.’ But nobody says, ‘I don’t want to hire a man of childbearing age.’”
Some Invisible Factors At Play
It makes sense that one obstacle to women’s proliferation has stemmed from a lack of computer science exposure in childhood, which can lead women to feel like they are at an insurmountable disadvantage once they start college. Expanding curriculum options and entry-level college courses, efforts being tested at schools like Harvey Mudd in California, may be one solution for leveling the playing field.
“You know unfortunately my take is that a lot of people who get into computers and programming start before college,” Sydell says, “which often does turn out to be young guys and so the women end up feeling intimidated.”
And it seems like computer science and engineering may currently be taught in a way that caters to how men think and conceptualize problems. “I remember people saying that for some reason guys are much more willing to work in the abstract for longer,” Sydell says. “I don’t know why this is, but women like to see pretty quickly that something they’re building is having an effect.”
This perspective could ultimately be a strength that draws women to coding, though, if other barriers are addressed. “It’s not that they can’t do the abstract,” Sydell says, “but once they see that programming can have this immediate effect they get more interested in it.”
Getting Private Views Out There
While reporting for her recent piece, Sydell attended a 25-person mentorship event with Sarah Allen for young entrepreneurs. After the event, the only three women in attendance came over to Allen and started chatting. “None of them talked about discrimination really,” Sydell says, but “they did talk about how they sometimes felt isolated. They all mentioned that in school they sought out a female colleague for support.” Yet even this small and understandable measure, they feared, could have unintended consequences. “They also debated whether it was possible to do too much networking with other women,” explains Sydell. “The problem is that the men have the larger networks and so you don’t want to limit your connections.”
Sydell has seen progress as an increasing number of hard working and qualified women enter tech, but she has also concluded that only a sustained, concerted effort will continue to draw women into the field. “I think one of the most important things that Sarah Allen said is find an industry where there isn’t sexism. If you get up to the higher echelons of anything the world is sexist. And the more money that’s involved, the more it seems to be guys. And what’s up with that?”
What It Feels Like To Be A Woman Programmer
We don’t hear from the women who are actually working in software often enough. Ellen Ullman, a former software engineer, recently penned an opinion piece in the New York Times called “How to be a ‘Woman Programmer’.” It’s an important firsthand account of what it actually feels like to be a woman working in technology--invaluable for men like me who will never subjectively know that actual experience.
I looked around and wondered, “Where are all the other women?” We women found ourselves nearly alone, outsiders in a culture that was sometimes boyishly puerile, sometimes rigorously hierarchical, occasionally friendly and welcoming. This strange illness meanwhile left the female survivors with an odd glow that made them too visible, scrutinized too closely, held to higher standards. It placed upon them the terrible burden of being not only good but the best.
Other parts of her article resonate with what we recently found in the gender gap by job title breakdown from Bright Labs: namely, that the more technical a job within the tech sector is, the wider the gender gap tends to be.
We get stalled at marketing and customer support, writing scripts for Web pages. Yet coding, looking into the algorithmic depths, getting close to the machine, is the driver of technology; and technology, in turn, is driving fundamental changes in personal, social and political life.
But perhaps the biggest takeaway for me and other male allies to women working in software, is this: It’s important to talk about the challenges facing women in software, but it’s just as important to recognize the achievements of women engineers as programmers, not merely as trailblazers. Ullman writes:
But none of it [experience as a programmer] qualified me as extraordinary in the great programmer scheme of things. What seems to have distinguished me is the fact that I was a “woman programmer.” The questions I am often asked about my career tend to concentrate not on how one learns to code but how a woman does.
Hard Numbers: The Actual Percentages Of Women In Tech Roles
Bright Labs has released new research to Co.Labs about which roles are most male-dominated, and some patterns begin to emerge.
This is one of the most complete snapshots of the gender gap in technology employment we’ve seen so far. Co.Labs readers have been eating up the slices of data on the gender gap we’ve been dishing out. It’s clear that "women in software" is a topic that begs for more coverage. So we got in touch with our friends at Bright Labs to provide us with some previously unreleased numbers on what the actual gender breakdown is by job title.
The first thing to keep in mind with these numbers is that job titles can be pretty arbitrary and may not actually reflect the kind of work being done by any given individual. With that said, there are a couple of interesting trends worth highlighting here. But first, the stats:

Let’s break down these numbers. First of all, it looks like tech support positions tend to bubble up and be the most of a dudefest: IT support, computer technician, network technician, and desktop support technician are all more than 90% male. Does this mean corporate suits feel more comfortable talking to a male IT geek about their problems with Outlook than a female IT worker? Or perhaps the IT help desk is a particularly unfriendly place for women to integrate? Either way, it’s important to note that these numbers are domestic; it would be interesting to see the gender breakdown in outsourced IT, or internationally.
On the other hand, “analyst” positions like data analyst, help desk analyst, and senior programmer analyst tend to be the least--though are still significantly--male-dominated, floating between 53.8% and 75% male. With these numbers, we’re starting to see a clearer picture now: The less a job deals with the back end of a development environment or network infrastructure, the more open (for whatever reason) it is to women working in that role.
One final interesting data point to note is that senior software developers are 89.5% male, while plain old software developers are only (“only”) 78.1% male.
What’s the gender breakdown for these positions like in your company? What do you make of these numbers? Do you have your own research you’d like to share? Tweet @jcassano and @FastCoLabs with your facts, insights, and opinions.
Why The Developing World Needs Women To Be Online
Want to improve economic conditions in developing countries? As usual, the best approach is to focus on women.
If women can’t get online, then there’s no chance they’ll get a job in software. Here at Co.Labs we’ve been on a number-crunching bit when it comes to women in software. So far we’ve taken a look at two important slices of data: perspectives on obstacles to getting more women in tech and how new tech jobs are mostly going to men. Now we take a look at the third piece of the puzzle: the gender gap in accessing the Internet.
Earlier this year, Intel released a massive study crammed full of useful research. It’s a lot to digest, so we’ve pulled out some of the most provocative trends.
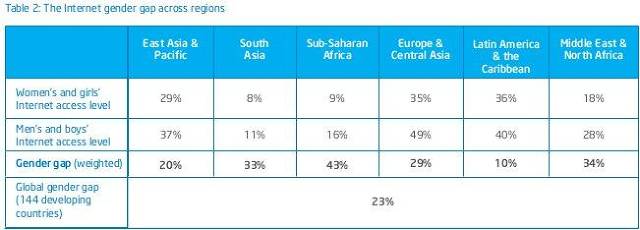
The report focuses on women’s access to the World Wide Web, particularly in developing countries. One consistent but unsurprising pattern is that the less economically well-off a country or region is, the wider the digital divide between women and men tends to be.
On average across the developing world, nearly 25 percent fewer women than men have access to the Internet, and the gender gap soars to nearly 45 percent in regions like sub-Saharan Africa. Even in rapidly growing economies, the gap is enormous. Nearly 35 percent fewer women than men in South Asia, the Middle East and North Africa have Internet access, and nearly 30 percent in parts of Europe and across Central Asia. In most higher-income countries, women’s Internet access only minimally lags that of men’s, and in countries such as France and the United States, women's access, in fact, exceeds men's.
Intel stresses that this is bad for business for two main reasons: first, the loss of revenue from online transactions and second, the reduction in economic opportunity for women who might use the Internet to find work. According to the report, there will organically be 450 million new women online by 2016--the report’s main recommendation is to boost this number by another 150 million in that time period. This will reportedly open up market opportunities of at least $50 billion.
Intel’s researchers also home in on the fact that 30% of women with reliable Internet access have used it to search for jobs or otherwise improve their economic standing. A lot of efforts to overcome the digital divide work narrowly on just getting more people online. That’s great, to be sure. But in a section called “not all access is equally empowering,” the authors write:
The Internet can convey numerous benefits to women, but unlocking these benefits depends on how deeply women engage online. “Fully engaging” on the Internet requires feeling conversant--knowing what to look for, how to search, and how to leverage networks, knowledge and services--as well having fast, unrestricted, reliable access.
Our study showed that the longer a woman had been using the Internet, the more likely she was to report concrete benefits such as earning additional income, applying for jobs, and helping with her studies. Users with multiple platforms to access the Internet were also more likely to report these concrete benefits than users of either computers or mobiles only.
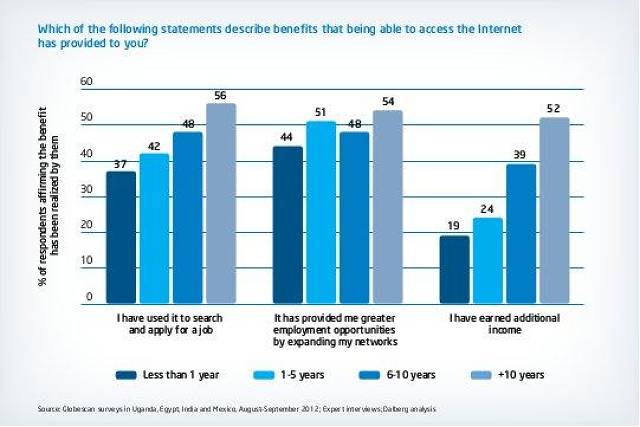
The report also features an interesting breakdown of the different demographic groups and how they are likely to access the Internet: computer-only, mobile-only, or multi-platform. In general, mobile-only users are younger women who use the Internet daily, but are unlikely to use it to apply for a job. Computer-only users (laptop or desktop) tended to be middle-income female homemakers and often use the Internet for education and study. Multi-platform users, naturally, tended to be wealthier women who use the Internet daily and are likely to use it for education and shopping.
How one accesses the Internet also affects one’s attitudes about it. Women who access the Internet through both mobile and computers, for instance, hold the strongest belief that Internet access is a fundamental human right. This suggests that there’s a positive feedback loop at work: The more regularly women access the web, the more they begin to see it as an integral piece of social fabric--something that everyone needs to be a part of.
This is good to know because if we’re serious about overcoming the gender gap in software, the first job needs to be getting more women around the world online. Computer programming is a skill that any individual, with enough access, can learn on their own to improve their economic standing. This is true even--and perhaps especially--in the developing world. If the next wave of new computer programmers is going to come from outside developed countries, then it’s imperative to get more women online now so that they can enter the job market on equal footing.
Is The Tech Gender Gap Widening?
Despite all of the increased attention the gender gap is receiving, new data suggests that it might be widening rather than shrinking. Spoiler alert: We need more women engineers.
The data doesn’t lie. For all the talk about tech becoming a less male-dominated space, women are still a vast minority in the industry. In fact, recent data from Bright.com suggests that the gender gap is widening--at least momentarily.
We recently covered a survey by the freelancing site Elance, an online marketplace for self-employment. That survey mostly focused on the attitudes of men and women freelancers towards how tech can become more open to women. A new survey from job search platform Bright tackles the nitty-gritty details of who’s actually snagging new tech jobs.
The number of jobs in the technology sector has grown a substantial 3.8% nationwide in just the first four months of 2013 (compared to the last four months of 2013). In April 2013, some of the known tech geographies where among the fastest growing regions in tech, including San Jose, Austin, San Francisco, Boston and Seattle, however other areas less well-known for their tech jobs also displayed strong growth, including Oklahoma City, Kansas City, Tucson, and Indianapolis.
Nothing new there. We know that tech is one of the country’s fastest-growing sectors, and that it tends to grow the most in traditional geographic hotbeds like the Bay Area. It is interesting to see that New York’s much-touted “Silicon Alley” didn’t make the growth cut while Kansas City continues to explode under the influence of Google Fiber.
The real question we’re interested in is, who are companies hiring to fill all these new jobs? The report tackled this question head on:
These jobs are trending to favor male job seekers. While the tech sector is predominantly male overall, an estimated 71% male, the titles displaying the largest increase in available jobs have also trended towards male-dominated roles, including Systems Administrators (89.7% male) and Senior Software Engineers (77.1% male).
Let’s take a moment to unpack these numbers. We know that men account for about three out of every four people working in tech right now. On top of that, the job areas that grew the most in the first four months of 2013 tended to favor men by an even larger percentage than the industry as a whole. If this trend keeps up, the gender gap may end up widening rather than shrinking, despite heightened awareness of the issue.
To be clear, we know the problem is probably even worse than it seems because a lot of the women who are counted as working in the tech sector often work in PR, HR, or marketing. The answer shouldn’t be to just keep hiring women in those roles. According to Bright Labs, the most in-demand job titles in April 2013 were all technical positions. Companies need to hire women engineers if they want the gender gap to shrink.
The war for engineering talent is so hot that companies are trying everything to lure top candidates. Sometimes, these incredible bonus packages are a great way of finding talent who will fit in with the team. Other times, the tactics become so gimmicky and specific that they’re almost guaranteed to screen out a diverse set of candidates.
Take, for example, Saatchi and Saatchi Tel Aviv’s recent decision to screen candidates for a software engineering position by conducting interviews inside Diablo III.
The idea to test skills like teamwork and thinking under pressure using a video game is worth exploring. The U.S. Army, for example, uses video games to help train soldiers how to recognize friendly people from insurgents disguised as civilians in Iraq and Afghanistan.
Choosing a specific game with no relation to the job other than the CEO’s preference, however, was probably not the way to go if the company wanted to have any shot at hiring a woman. Technology is already a male-dominated field, especially in Israel. Moreover, Diablo III’s playerbase is 69% male, meaning that by choosing the game you’ve already narrowed down the pool to an incredibly homogenous group.
Even if you did find a qualified woman gamer-developer, there’s another problem with conducting in-game interviews that most men would never even think about. Due to a combination of their relative scarcity and the anonymous nature of online gaming, women who play Internet games and identify themselves as such face a constant barrage of sexist trash-talking from their male counterparts. The problem is so severe that some women have created entire sites to document the misogyny they face playing online on a regular basis. Given the stigma attached to female gamers, it wouldn’t be shocking if women didn’t want to participate in an interview where their potential boss was giving them orders over the same system so many jerks use to berate them.
Although it’s tempting to search for new and inventive ways to find candidates, companies have to be careful not to automatically weed out too many qualified candidates just by the interview criteria. There’s a fine line between offering perks that help you find someone who will fit well on the team and searching for such specific traits that you’re almost guaranteed to find someone exactly like yourself. Unfortunately, Saatchi crossed that line.
This update was contributed by Gabe Stein.
According to a survey conducted by Elance, the greatest deterrent to getting more women in technology fields is a lack of female role models. Elance is a popular platform for freelancers, so survey respondents come primarily from that share of the tech marketplace. And some questions are specific to working from home. Still, it’s probably a safe assumption that a lot of the same trends apply for women working in technology fields whether remotely or in-office.
It’s definitely worth reading through the results of this (fairly short) survey. Here are three stats we’ve pulled out for you:
- 66 percent say that for women to be successful in tech will require equal pay for women and men with same skillsets
- Only 22 percent of respondents believe technology needs to be made more “glamorous” or “cool” in order to appeal to women
- 80 percent are “optimistic” or “extremely optimistic” about the future of women in technology
Female readers: Do these figures resonate with you? The most interesting stat here is the one about unequal pay, because it demonstrates that the women responding to this survey expect to get paid less off the bat, even in more progressive companies. Also--it’s telling that nearly a quarter of respondents don’t find technology “cool enough” to compete with careers in more feminine organizations. Help us unpack what these stats mean by sharing your take on Twitter.
A recent NPR segment, “Blazing The Trail For Female Programmers,” profiled the lead developer of Flash video, Sarah Allen. It’s part of an ongoing NPR series called “The Changing Lives of Women.” NPR talked with Allen about what it means to work in a field where only 20 percent of her peers are women.
Today Allen is CEO of mobile design & development outfit Blazing Cloud. In addition to Blazing Cloud’s volume of work speaking for itself, Allen is also getting business from startups who value their genuine emphasis on diversity, as opposed to just hiring women as “window dressing.”
Allen reflects on the decades she spent being the only woman on a development team and how things still haven’t changed too much. She tells a story about being being one of six women at a 200 person Ruby on Rails conference a few years back. Coming out of that experience Allen started RailsBridge, an organization aiming to increase diversity in tech through free workshops for “women and their friends.”
She also emphatically makes the point that the issue is a lack of supporting for women who already want to get into tech:
We've really proven that demand is not a problem. Every single workshop we've ever held has had a waiting list.
There are lots of other interesting moments in this quick 8-minute segment: According to NPR, the proportion of women studying computer science has actually decreased since the mid-20th century (that’s ponderous stat #4, for those counting). While you’re listening, also check out the April 29th broadcast of NPR’s All Things Considered for a complementary segment about Harvey Mudd’s efforts to get more women in computer science degree programs.
Should all-male software companies be on some kind of wall of shame? Here at Co.Labs we’ve celebrated the success of specific companies that have actively sought to increase diversity within the programming community. But what about those companies with particularly egregious records? Is it really so bad to have an organization that’s all one sex?
The creators of a blog called 100% Men think so, which is why they’ve put the spotlight on IFTTT, Posterous, Autonomy (an HP subsidiary), and the dating site Couple.me--all of which boast about as much gender diversity as a Freemasons meeting. (In fairness, Posterous was only 100 percent men as of 2011, and the company is being shuttered anyway, but to their credit they now they have two women on staff: one engineer and the office manager.)
It seems like a total no-brainer for a dating product to have a gender mix on the design team, doesn’t it? Perhaps that’s why no one’s heard of Couple.me. Read previous updates to this story below.
Rails Girls Summer of Code (RGSoC) was started by Berlin Rails Girls organizers to help Rails Girls get into open source, a focus that distinguishes it from Google’s original Summer of Code. Ruby on Rails is a full-stack development language that you can learn more about here.
Just as in Google Summer of Code and Ruby Summer of Code, students will be paid so they're free to work on Open Source projects for a few months. Unlike those programs, the Rails Girls Summer of Code is about helping students to further expand their knowledge and skills by contributing to a great Open Source project (rather than producing highly sophisticated code).
Targeting women in tech is great, and helping them become active, productive members of the vibrant Rails and open source communities makes this program particularly exciting. To get involved as a student or mentor, write to summer-of-code@railsgirls.com or catch RGSoC on Twitter.
Stacey Mulcahy wrote a letter to her 8 year old niece and posted it online. Why does that matter? Well Mulcahy—aka @bitchwhocodes—is a developer who has personally come up against the shortcomings of the tech community when it comes to gender equality. Inspired by her 8-year-old niece’s decision to become a game developer when she grows up, Mulcahy wrote this letter“to a future woman in tech.” It’s full of hopes for her niece and for the developer world in general:
I hope that when you attend a meeting that is mostly male, that you never get asked why you are not taking meeting notes. I hope you say "fuck this" more than "it's okay".
...I hope that skill will always be held in higher esteem than your gender--if you had no skill, you would not be part of the discussion, and your gender is simply a modifier.
...I hope that no one ever tells you to "deal with it," "relax," or "ease up" because you refuse to laugh at something that simply is not funny.
...I hope that you attend conferences and find yourself complaining about long lines for the bathroom.
A lot of the lines in this letter will be familiar with anyone who follows even the slightest the grievances of women in tech. But it’s a powerfully original way of framing the issue, by focusing on the positive vision of the kind of developer community Mulcahy would like to be a part of, rather than just railing against the shortcomings of the one that currently exists—it's empowering. (Hat tip to @NGA_Anita.)
We can talk about the gender divide in tech all day, but it’s also important to celebrate the achievements of women in software. In fact, if it weren’t for the work of one woman, Ada Lovelace, computers as we think of them today might not exist. Lovelace worked closely with Charles Babbage on his early mechanical computer designs. Although today Babbage is considered the "father of computing," it was actually Lovelace who is believed to have written the first computer program. She also imagined computers as more than just calculating machines, influencing the thought of several pioneers in modern computing.
Stevens Institute of Technology is holding a conference celebrating the achievements and legacies of Ada Lovelace on October 18, 2013. Proposals for papers are due May 14. From the institute:
An interdisciplinary conference celebrating the achievements and legacies of the poet Lord Byron’s only known legitimate child, Ada Byron King, Countess of Lovelace (1815-1852), will take place at Stevens Institute of Technology (Hoboken, New Jersey) on 18 October 2013. This conference will coincide with the week celebrating Ada Lovelace Day, a global event for women in Science, Technology, Engineering, and Mathematics (STEM). All aspects of the achievements and legacies of Ada Lovelace will be considered, including but not limited to:
- Lovelace as Translator and/or Collaborator
- Technology in the Long Nineteenth Century
- Women in Computing: Past/Present/Future
- Women in STEM
- Ada Lovelace and her Circle
So if you care about women in software, then, now, or in the future go ahead and submit a paper. It’s a good way to honor the legacy of the world’s first coder -- a woman.
Previous Updates To This Story
For those who missed it, "donglegate," as Wired dubbed it, is the latest blowup after a display of sexism in the coding community. Although some people, including women in tech, took issue with the way Adria Richards handled the situation, Wired's Alice Marwick puts it in context very bleakly:
Regardless of the nuances of the incident, the fact remains that Richards faced a gargantuan backlash that included death threats, rape threats, a flood of racist and sexually violent speech, a DDOS attack on her employer--and a photoshopped picture of a naked, bound, decapitated woman. The use of mob justice to punish women who advocate feminist ideals is nothing new, but why does this happen so regularly when women criticize the tech industry? Just stating that the tech industry has a sexism problem--something that's supported by reams of scholarly evidence--riles up the trolls.
Jezebel also chimed in, pointing out the how these kinds of jokes are possible and seem normal because of how much of a dudefest tech is. It seems particularly egregious that these guys made these jokes right when the speaker was talking about bridging the gender gap in tech.
Richards was distracted, mid-seminar, by a couple of tech bros sitting behind her making some shitty sexual puns about "dongles" and "forking." (She blogged about the full chronology of events here.) Richards did not enjoy the jokes. She especially did not enjoy the disrespect shown to the speaker, who happened to be specifically, at that moment, addressing programs designed to make the tech community more welcoming to women. Meanwhile, in the audience--Richards's photos reveal a sea of men--a couple of dudes felt 100% comfortable cracking the kind of crude jokes that people generally reserve for their home turf. And that's because, to a lot of dudes, tech is a space owned by men.
Bruce Byfield, who has written extensively on all things free & open source, gives an overview of sexism in the FOSS community. As a subset of the broader development community, FOSS has a lot of great things going for it because of its transparency and emphasis on collaboration. Unfortunately it still shares many of the same problems when it comes to gender. Byfield takes an informative look at initiatives that are trying to fix the gender imbalance, like the Geek Feminism Wiki, Ada Initiative, and Ubuntu Code of Conduct.
Carla Schroder credits Ubuntu for its all-purpose code of conduct, which she calls "a radical departure from the dominant 'freedom to be a jerk' ethos that prevailed before." As a result, Schroder adds, "Ubuntu has also attracted large numbers of contributors and users from more diverse walks of life than other distros.
However, in the last two years, FOSS feminism has paid special attention to anti-harassment policies for conferences. Most of this work has been developed by the Ada Initiative, an offshoot of the Geek Feminism Wiki, which has developed templates for policies that can be used either unmodified or as starting points for discussion.
The rationale offered for this emphasis is that anti-harassment policies can be a starting point for changing other aspects of the community.
All in all a thorough and well-reasoned piece worth a read (even if the pagination on datamation is ridiculously annoying).
Ashe Dryden, a Drupal and Rails developer, did the software community a huge favor by starting to answer the question "How can I help tech be less sexist?" She gives concrete, applicable steps that people can take to make conferences more diverse, like:
Anonymize and remove gendered pronouns from abstracts/bios before handing the data over to your proposal review committee. Someone who is outside of your proposal reviewing committee should be assigned this task.
Pretty simple, but makes a huge difference. Dryden's post is full of tidbits like that. It also includes a pretty thorough list of different marginalized populations, going far beyond gender diversity to include, for example, physical disability and economic status. But women in tech is still the focus of what Dryden is writing about.
The headline of this article in Forbes elides individual (and organizational) responsibility by saying that women are "accidentally" excluded from tech. That said, it still makes a great point that tools like Codecademy are democratizing technology and thereby removing a lot of the traditional barriers to women, like it being hard to find mentorship in a boy's club.
Dani Landers, a transgender woman game developer, gives an account of how her identity informs her game design decisions in Bloom, a game currently vying for funding on Kickstarter.
It's no secret that the games industry, by and large, lacks diversity. In this case, that is gender diversity. This is actually a huge shame as it limits the stories and points of views different types of people bring to the collective table of gaming.
Landers contrasts the way she handles representation of female characters and motherhood with the way major video game studios do, which is pretty obvious in her artwork.
The differences in the way I create concept art and models is pretty self-explanatory. Basically, notice how the female characters aren't half naked with giant breasts? Yea, this is a pretty easy one to be aware of...I'm kind of surprised this is even "different" to treat them with that level of respect.

The influential gaming site Penny Arcade picked up the story, with a really interesting take on how gaming can be a safe haven for certain marginalized populations.
Games themselves may offer a safe place for transgender, genderqueer, questioning, or other LGBT community individuals, but the gaming community has been less receptive. When Landers was promoting her game in one gaming community forum, users hijacked the thread and began posting "tranny porn," telling Landers she should find new work in the adult film industry.
Articles and features on gaming sites that bring up gender representation of any kind, be it transgender or otherwise, is typically met with the 'Why is this important?' 'How is this relevant to video games?' style responses. It should be apparent by now that games can be far more than just entertainment to some individuals. To some, it's a necessary escape, or a safe haven where the question of "Who am i?" can be safely explored.
So, a pretty prime example of women being reduced to sexual objects in the technology world is this article on Complex, "The 40 Hottest Women in Tech". At first glance the article is a weird mix of acknowledging sexism in tech followed by outright sexism from a publication covering tech. It begins:
Technology has been a boy's club for most of its existence. Just another unfortunate repercussion of the patriarchy. But that's been slowly changing, and over the last decade we've seen a number of wonderful, intelligent, and cunning women make inspiring strides in the field of technology. Through web development, social media, space exploration, and video game design, we see the world of tech becoming a more equal playing field. Here are 40 women we admire doing work in the field of innovation.
Followed by a slideshow of scantily clad women or typical "hot" women, including noting that one of them was a Playboy playmate. Commenters on the piece were justifiably outraged, writing:
How can you open with "sure, tech hasn't been friendly to women for ages, but it's better now!" and then proceed to objectify the women who have fought through this bullshit? Do you not see that you're only perpetuating the toxic culture?
And:
Funny you would mention patriarchy in your opening paragraph, then proceed to perpetuate it by subjecting all of the hardworking and talented women in this field to, effectively, a 'hot-or-not' list. Shameful.
It turns out, though, that the author of this piece didn't want it turn out that way:
I was assigned to write the 50 Hottest Women in Tech by Complex and it really bummed me out, because the idea of perpetrating the same old gender divisions in an area like tech - which has predominantly been a boy's club throughout history - seemed like kind of a messed up thing to do. It represents the most banal form of internet content that exists. But it's hard to say no to a paycheck.
So what I tried to do was see if it was possible to make something called "The 50 Hottest Women in Tech" earnest and empowering and an actual good thing. I pretty much only included normal looking women, who were involved in something really crucial or exciting in the tech space. I made no allusions to their looks in the blurbs, and ended up with simply a long list of very exciting women.
Of course when the piece actually ran, I discovered that over half of the women I had included were replaced with people like Morgan Webb, complete with the usual lascivious dialogue. Sigh. It's hard to win when you're writing for Complex, but please know that I tried.
That explains why tech-entertainment celebs are mixed in with actual female technology innovators like Gina Trapani and Marissa Mayer. It's the mark of a bad publication that it would not only assign a piece like this in the first place but that it would so drastically alter it after the fact. Fortunately, people in technology fields weren't buying what Complex was selling, as evidenced by this tweet and this tweet:


Stay tuned as coverage continues!
[Image: Flickr user Drazz]